Table of Contents
Connecting GitLab to LinearB
Connect GitLab to LinearB using a Personal Access Token (PAT) to sync repositories, merge requests, and Git activity.
If you do not have administrative access to your GitLab repository or lack the required permissions to authenticate GitLab with LinearB via OAuth, you can still connect using a GitLab Personal Access Token (PAT).
To generate a PAT that grants LinearB the required access, you must be an organization owner or have Maintainer or Owner permissions for the relevant repositories.
Follow the steps below to generate your token and connect GitLab to LinearB.
Summary
What this guide covers
- Generating a GitLab Personal Access Token (PAT)
- Selecting the required scopes (permissions)
- Connecting GitLab to LinearB using the PAT
- Reauthorizing the PAT in LinearB (expired token)
- Troubleshooting common issues
Before you begin
- GitLab account with Maintainer or Owner permissions (or organization owner)
- LinearB Admin role
Step 1. Generate a Personal Access Token (PAT) in GitLab
To connect GitLab, first create a Personal Access Token:
- Log in to GitLab.
- On the left sidebar, select your avatar.
- Select Edit profile.
- On the left sidebar, select Access tokens.
- Select Add new token.
- In Token name, enter a name for the token.
- In Token description, enter a description (for example, LinearB Integration).
-
In Expiration date, enter an expiration date for the token.
The token expires on that date at midnight UTC.
If you do not enter an expiry date, the expiry date is automatically set to 365 days later than the current date.
By default, this date can be a maximum of 365 days later than the current date. In GitLab 17.6 or later, you can extend this limit to 400 days.
If you encounter issues due to an expired token, contact support@linearb.io. - Select the required scopes (permissions).
Scope |
Access |
|
Complete read/write access to the API, including groups and projects, registries, and repositories (Git over HTTP). |
|
Read-only access to the authenticated user’s profile through |
|
Read access to the API, including groups and projects. |
|
Read-only access to repositories on private projects using Git over HTTP or Repository Files API. |
|
Read-write access to repositories on private projects using Git over HTTP. |
|
Read-only (pull) access to container registry images (when enabled). |
|
Read-write (push) access to container registry images (when enabled). |
|
Read-only (pull) access to images via dependency proxy (when enabled). |
|
Pull, push, and delete access to images via dependency proxy (when enabled). |
|
Perform API actions as any user (admin only). |
|
Perform admin API actions when Admin Mode is enabled (Self-Managed only). |
|
Create runners. |
|
Manage runners. |
|
API actions for AI features such as GitLab Duo, Code Suggestions, and Duo Chat (scope behavior varies by environment/version). |
|
Kubernetes API calls using the agent for Kubernetes. |
|
Rotate this token using the personal access token API (does not rotate other tokens). |
|
Download Service Ping payload through the API (admin only). |
- Select Create personal access token.
- Save the token somewhere safe. After you leave the page, you can’t view it again.
For more details, see the GitLab Personal Access Token Documentation .
Optional: Real-time updates with write_repository
LinearB requires write_repository permissions to configure webhooks for real-time data collection. Without this permission, LinearB still works, but data updates may be delayed by up to 2 hours.
- This delay can impact metric accuracy and increase wait times for WorkerB notifications (for example, PR review requests).
Alternative authentication method
If write_repository cannot be granted due to security restrictions, consider using a service account:
- Create a GitLab service account with admin permissions for all relevant repositories.
- If applicable, use an existing “global admins” group to manage access.
- Connect the service account to LinearB using OAuth.
For more details, see GitLab’s documentation on creating groups in GitLab.
Step 2. Connect GitLab to LinearB
After generating a PAT, connect it in LinearB:
- In LinearB, go to Settings → Company Settings and select the Git tab.
- Click Add Integration.
- Select GitLab as your Git provider.
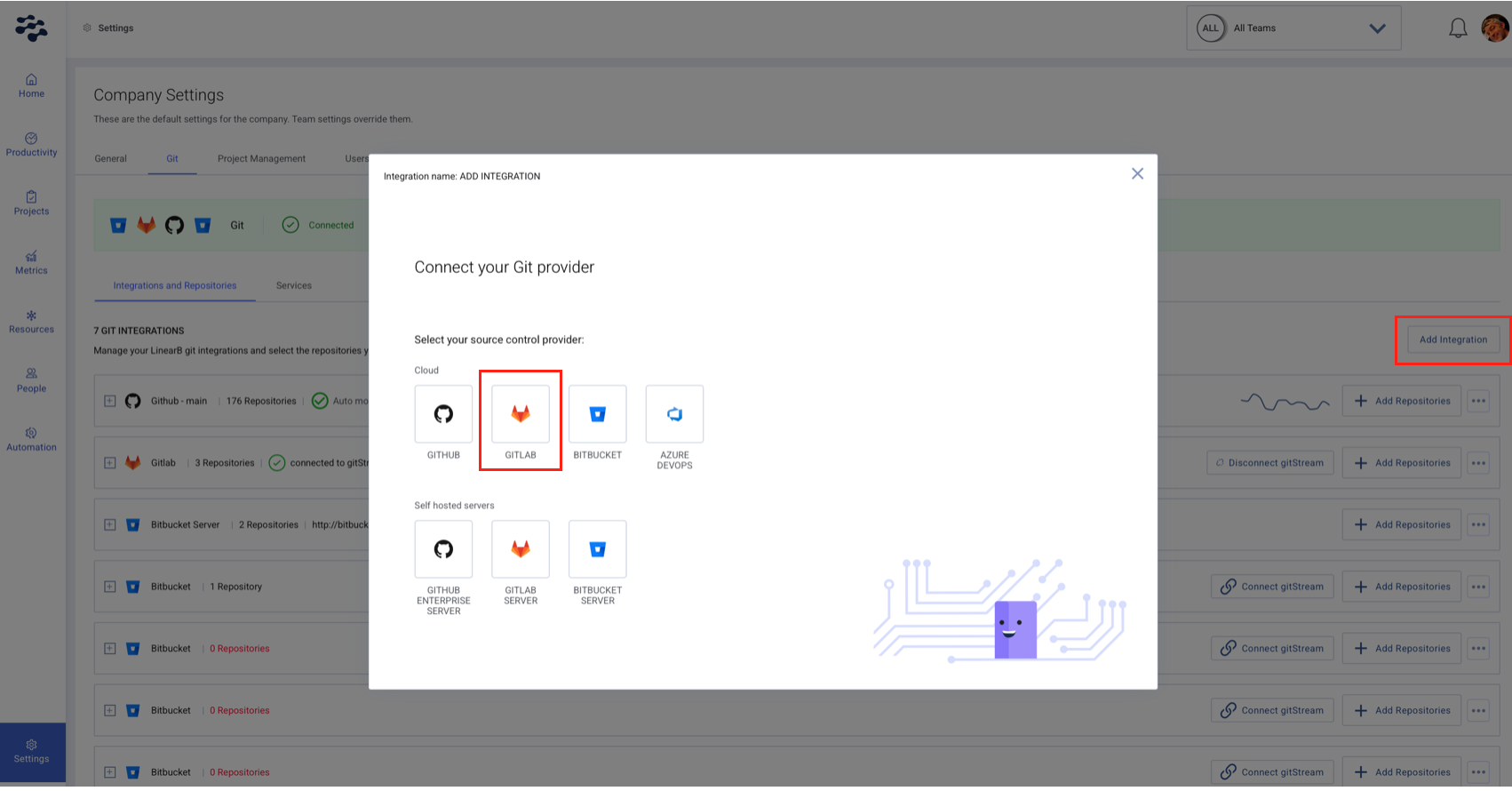
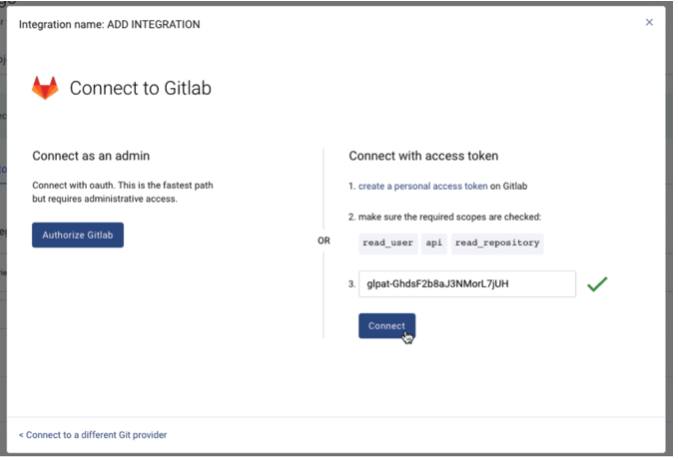
- Paste your Personal Access Token (PAT) into the required field.
- Click Connect. LinearB will begin processing your GitLab repositories.
Step 3. Reauthorize your GitLab token in LinearB (expired token)
If your GitLab token expires, generate a new token and update it in LinearB:
- Generate a new token by following Step 1 above.
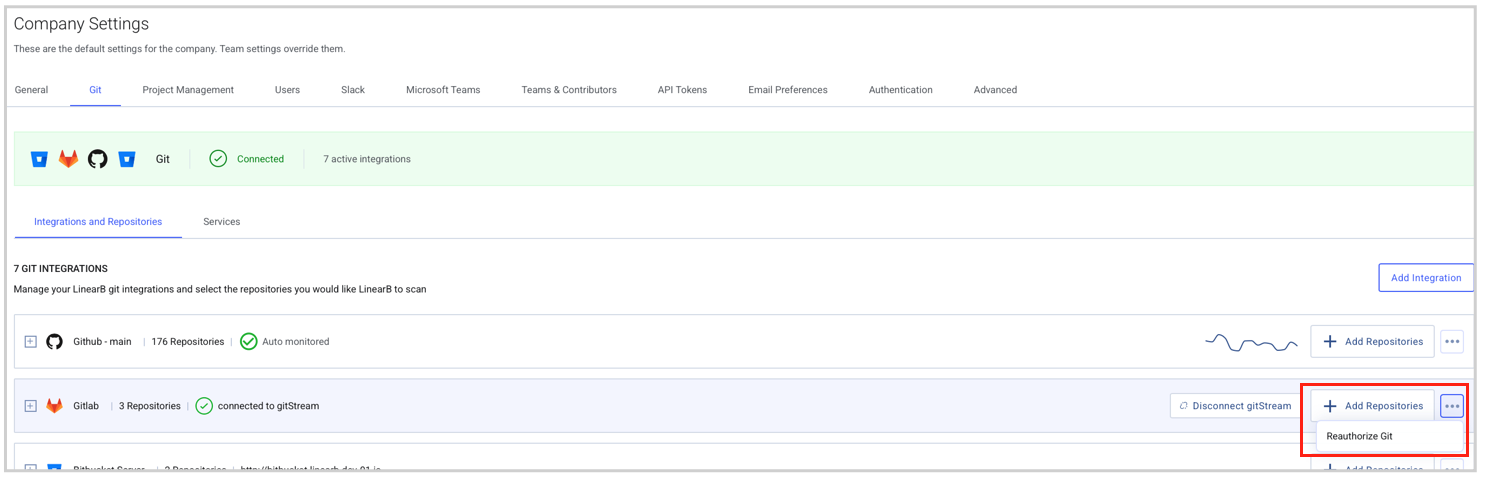
- In LinearB, go to Company Settings and select the Git tab.
- Click the three-dot menu next to your existing GitLab connection.
- Select Reauthorize Git and enter your new token.
Once updated, LinearB resumes processing your GitLab data.
Troubleshooting & support
- Ensure the PAT includes the required scopes (permissions).
- Verify your GitLab account has access to the repositories you want to connect.
- If issues persist, contact LinearB Support or join the Dev Interrupted Discord Server.
Related guides
Need assistance?
Visit our HelpDocs Support Page.
How did we do?