Configuring SAML SSO with GSuite
To configure SAML Single Sign On (SSO) authentication for your users using GSuite as your identity provider (IDP), you will need: Accessing SSO Config in LinearB and Google. Access to the Google Admi…
To configure SAML Single Sign On (SSO) authentication for your users using GSuite as your identity provider (IDP), you will need:
Accessing SSO Config in LinearB and Google
- Access to the Google Admin Console for your domain
- Admin access to LinearB
To configure SSO in LinearB, navigate to the Company Settings page using the gear icon, and then to the Single Sign-On tab (link).
In another tab, navigate to the Google Admin console and go to Apps > Web and Mobile Apps using the left-hand hamburger menu:
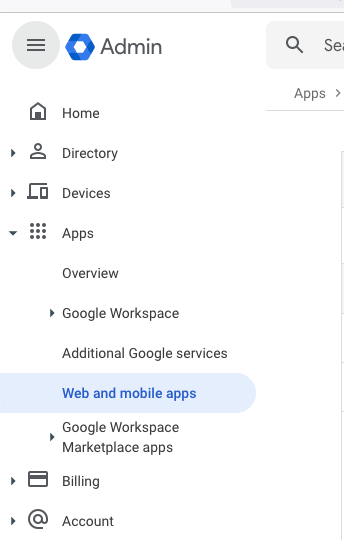
From there, select Add app > Add custom SAML app.
Configuring SAML in LinearB and Google
Type "LinearB" as the app name, add a description for your users if desired, and attach an icon if needed. Click to go to the next screen, and you will be presented with your Google metadata. Then complete the following:
- Copy the Google
SSO URLand paste it in to LinearBProvider Sign-onfield - Ensure that the LinearB
Provider Issuerfield is set tohttps://app.linearb.io/login - Enter your domain in the
Organization Email Domainfield (use the domain as it appears after the @ sign in your corporate email addresses) - Copy the Google
Certificatefield and paste it in the LinearBCertificatefield - In Google, click the Continue button to navigate to Service provider details
- Copy the LinearB
Callback URLand paste it in the GoogleACS URLfield - Paste
https://app.linearb.io/loginin to Google as theEntity IDvalue - In Google, leave
Start URLblank and leaveSigned responseunchecked - In Google, select
EMAILas theName IDformat, and make sure theName IDvalue is mapped to your user's email addresses (by default,Basic Information > Primary email) - In Google, click Continue to continue to
Attribute mapping. Leave this blank and click the Finish button. - Click the Save button in LinearB. It will prompt you to log in via Google—close that window for now rather than logging in. (If you attempt to log in at this point, the login will fail with a 403 error.)
Enabling User Access in Google
Google defaults to leaving a new SAML app disabled for all users, so you will need to enable it. From the Web and Mobile Apps screen in Google, you will be able to click on LinearB to open its settings. On that settings page, you should see a User Access panel:
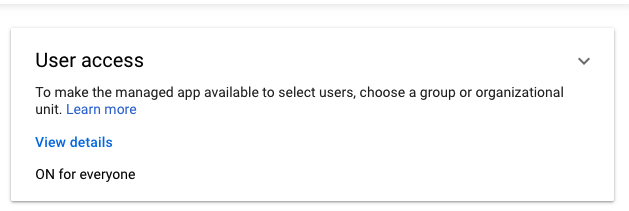
Click on the User Access panel to open up access settings. From there, you can either set the app to ON for everyone and save, or enable it for individual organizational units or groups.
Once you've made your access changes, click Save. On the display page for the SAML app, confirm that the app is on for all or some users. Then, click the TEST SAML LOGIN button:
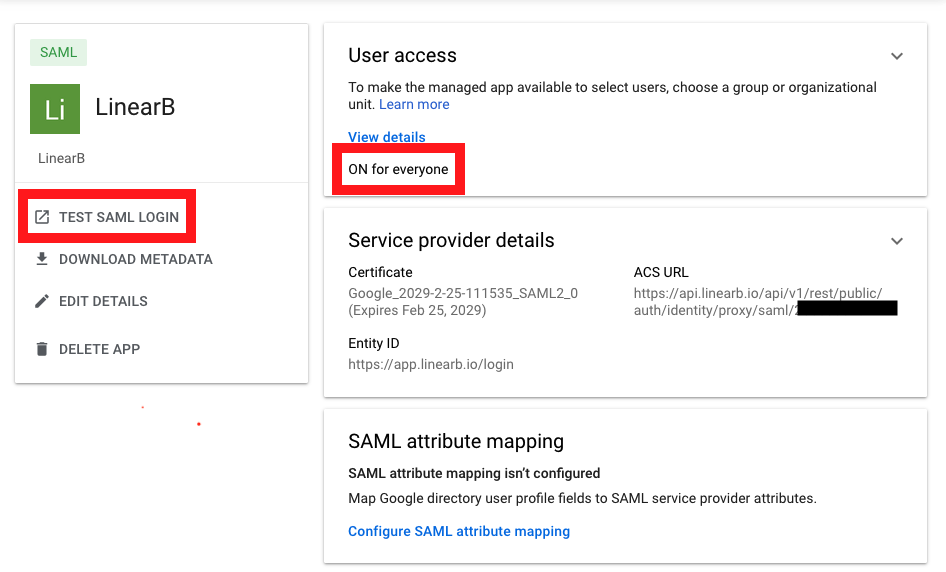
You may receive a popup from Google saying that the app is not yet provisioned for your user. If this is incorrect, wait five minutes and click the TEST SAML LOGIN button again. (You may need to do this a few times—enabling access to the app in Google can take several minutes to propagate.)
Once you are able to click the button without the popup warning, you should be logged in to LinearB, and will see a popup confirming that login access has been validated.
Enforcing SSO login
If you want to require your teammates to log in using SAML SSO, then return to the Single Sign-On tab in Company Settings. Click the Edit button at the bottom of the page. Check the Team members will only be able to access LinearB using your SSO provider checkbox, and click Save.
How did we do?
